NIS2 Directive: the path to improved cyber security

The amount of data generated and stored is growing exponentially. Digital transformation, societal interconnectedness, AI, and our vast online activities contribute to this data flood. Data centers play a critical role in enabling this growth. As the volume of sensitive data increases, data centers must ensure continuous service availability and robust protection measures.
Recognising the importance of data management and governance, the European Union has introduced the EU Network and Information Security Directive (NIS2), an update of the existing NIS directive. NIS2 aims to achieve a high common level of cyber security across the EU. This article focuses on the general scope of NIS2 and its implications for data centers.
Understanding (the structure of) NIS 2
NIS2 broadens its scope to include more sectors beyond traditional critical infrastructure. This now explicitly covers data centers, but also healthcare, financial services, and the public administration sector, reflecting the growing interdependence of digital services.
NIS2 requires companies to comply with several security measures, often demonstrated by certifications like Cyber Essentials or ISO 27001, which have the advantage of being presumed compliant with NIS 2. They focus on 3 main articles of NIS2:
- Article 20: Governance
- Article 21: Cyber security risk-management measures
- Article 22: Reporting obligations
Governance is a significant aspect of NIS2, emphasising the responsibility of all company members. Management bodies are now more accountable for security breaches, and training is crucial for understanding cyber security’s gravity. Every employee must recognise that a cyber security issue at their level can impact the entire organisation. But what are risk-management measures to take to be NIS 2 compliant?
10 cyber security risk-management measures
The general assumption is that security breaches can happen to anyone at any time. The purpose of the cyber security risk-management measures is to protect network and information systems, and the physical environment of these systems from incidents. This can mean an array of things, but to make this more digestible, NIS2 hands 10 thematic areas to us, which form the minimum measures.
- Risk assessments and security policies for information systems: companies must have clear cyber security policies, covering everything from asset inventories to disaster recovery procedures.
- Incident handling: this is defined as actions to prevent, detect, analyse, contain, and recover from incidents. Policies should include detection procedures, reporting phases (initial report, incident report, detailed report), and communication protocols. For example, incident reporting can include information like the affected assets, the date and time of the detection, the detection method, the immediate actions, and internal and external communications related to the incident.
- Business continuity plans: these ensure critical business functions continue during and after disruptions, with policies for updating backups and assigning recovery roles. A strong business continuity plan can limit the effect of a breach on your own business, but also your clients’.
- Supply chain security: supply chain attacks are described as one of the factors that contributes to the increase in ransomware attacks. NIS2 emphasises the importance of security in supply chains, particularly for SMEs, which are often targets for attacks affecting their operations and their clients. They often have fewer security resources and less rigid measures on risk and crisis management. Companies must install security measures that fit the vulnerabilities of each direct supplier and assess the overall security level for all suppliers.
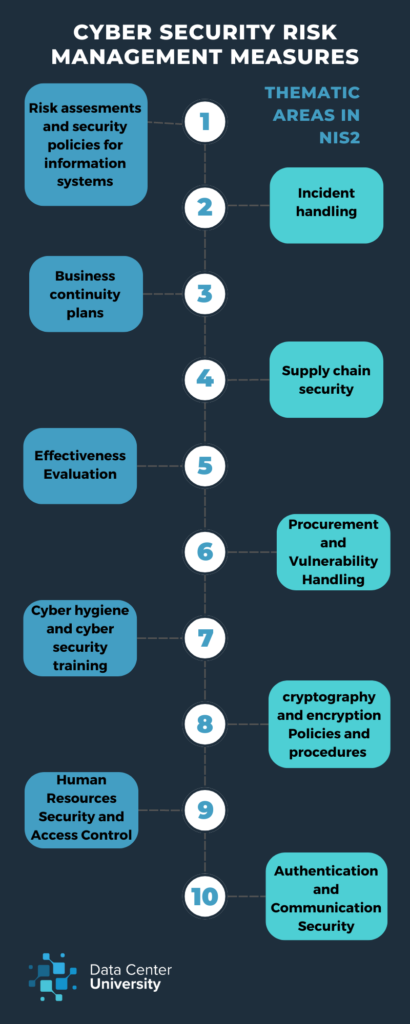
- Effectiveness Evaluation: policies and procedures for evaluating the effectiveness of cyber security risk-management measures go hand in hand with continuous improvement and compliance monitoring. This is achieved through regular internal audits and evaluations by competent authorities who ensure effective cyber security risk management.
- Procurement and Vulnerability Handling: security around the procurement of systems and the development and operation of systems is essential. More specifically, we can discuss vulnerability handling and a vulnerability disclosure, which lays the emphasis on the reporting obligation. Coordination between entities is, again, of utmost importance when vulnerabilities are discovered.
- Cyber hygiene and cyber security training: it’s mandatory to train and management bodies on a regular basis, covering software updates, device configuration, and phishing. Data centers should also inform their clients of significant cyber threats and of possible measures that they can take to safeguard their devices and communications.
- Policies and procedures regarding the use of cryptography and encryption is the next thematic area. Cryptography should be used in a manner that aligns with the information classification and risk analysis results, then it can provide the necessary environment for protecting data confidentiality, authenticity and integrity. The use of encryption technologies is also mandatory.
- Human Resources Security and Access Control: Procedures for employees with access to sensitive data, including background checks and access control methods like ID cards and biometric data.
- Authentication and Communication Security: Multi-factor authentication, secured communication systems, and continuous authentication solutions are crucial for managing user identities and protecting authentication information.
NIS2 represents a critical step forward in bolstering Europe’s cyber security landscape. For the data center sector, this directive brings both challenges and opportunities. By adhering to the requirements and fostering a proactive security culture, data centers can enhance their resilience against cyber threats and contribute to the overall security of the digital ecosystem.
Data centers must take proactive steps to align with NIS2, ensuring they are well-prepared to handle the evolving cyber security landscape. For further guidance, data centers can consult with cyber security experts or refer to the official documentation provided by the European Commission.





Responses